Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124


When administrators search for WordPress MD5 hash decrypt methods, they’re typically facing one of three scenarios:
ALSO READ: How to block website on Safari
Before proceeding, a critical disclaimer:
“Attempting to decrypt passwords without explicit authorization violates computer crime laws in most jurisdictions, including the US Computer Fraud and Abuse Act and EU GDPR regulations.”
— United States Department of Justice
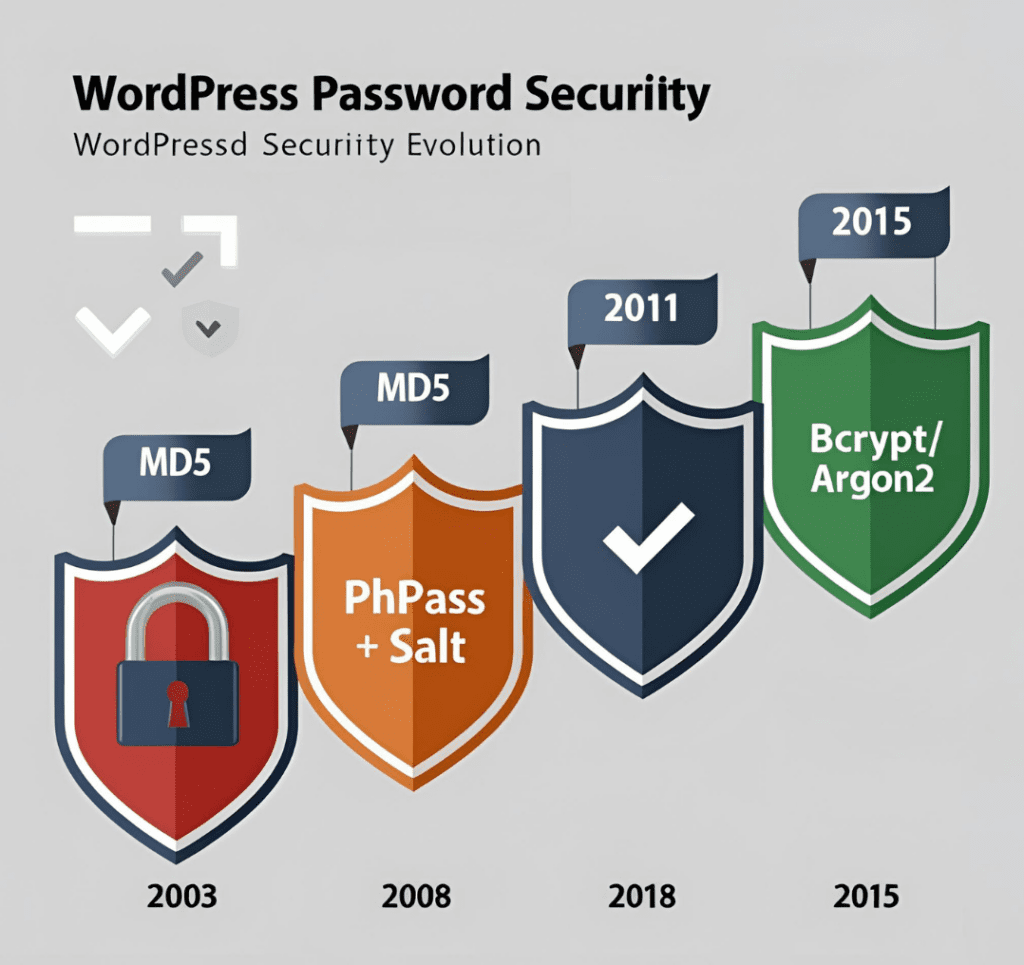
Early WordPress versions stored passwords as unsalted MD5 hashes. A user with password “admin123” would have this database entry:
user_pass = '0192023a7bbd73250516f069df18b500'
Vulnerabilities:
WordPress 2.5 introduced the PHPass framework, creating hashes like:
$P$B12345678ahjksdfhASDF.123sdafkjsdaf
Key Improvements:
Current versions prioritize:
Example of a modern hash:
$2y$10$N9qo8uLOickgx2ZMRZoMy.MKb7i7gPrE1ZI4gXo3XIq3P8a6ZJ3qK
MD5 is a one-way cryptographic hash function, meaning:
Precomputed tables of common passwords and their hashes. Tools:
Limitation: Fails against salted hashes or strong passwords.
Example command to crack an unsalted MD5:
hashcat -m 0 -a 3 5f4dcc3b5aa765d61d8327deb882cf99 ?l?l?l?l?l?l
This attempts all 6-character lowercase combinations.
Hardware Performance:
| Hardware | Hashes/Second |
|---|---|
| RTX 4090 | 164.1 GH/s |
| 8x A100 | 1.2 TH/s |
Source: Hashcat Benchmarks
Combine with tools like:
Pro Tip: Always start with rules-based mutations (-r flag in Hashcat) for better results.
For sites where you have admin access:
// functions.php temporary solution wp_set_password( 'new_password', $user_id );
Better Alternative: Use WP-CLI:
wp user update 1 --user_pass="newpassword"
UPDATE wp_users
SET user_pass = MD5('temporary123')
WHERE user_login = 'admin';
Use WordPress’s password generator:
require_once('wp-includes/class-phpass.php');
$wp_hasher = new PasswordHash(8, true);
$new_hash = $wp_hasher->HashPassword('newpassword');
For authorized investigations:
Legal Requirement: Always maintain a documented chain of custody.
Add to wp-config.php:
define('FORCE_PASSWORD_RESET', true);
Via plugins like:
Essential plugins:
Solution: Use a custom script that:
Check against haveibeenpwned.com’s API:
$hash_prefix = substr(md5($password), 0, 5);
$response = file_get_contents("https://api.pwnedpasswords.com/range/$hash_prefix");
Consider:
While the search for WordPress MD5 hash decrypt solutions persists, modern security best practices dictate:
For legacy systems, always:
✔ Document all access attempts
✔ Use legal recovery methods
✔ Educate stakeholders on risks
Final Resource: NIST Special Publication 800-63B for latest password guidelines.